Intelligence
We invite you to browse our curated collection of insights and analysis — all developed by LNW team members.
Our Featured Content

Commentary Q2 2024: Beyond the Market as Monolith
With geopolitical and economic risks both increasing, LNW CIO Ron G. Albahary, CFA® explains how we are taking advantage of the differentials among and within markets and asset classes to keep portfolios on course. Click here for the Executive Summary or download full paper below.

How We Work with Co-Trustees
We have a distinct advantage working with co-trustees because we tend to have existing relationships not only with our clients, but also their family members and their outside advisors.” – Kristi Mathisen, JD, CPA, PFS Trusts at LNW are built on relationships that grow and are reinforced over time. One of the key relationships we

Raising Money Wise Kids
It’s not their teachers nor their friends. Parents are by far the single biggest influence on how kids think about money. From pre-school through high school, here are thoughtful ways that parents can instill in their children confidence and responsibility about money before they leave home.
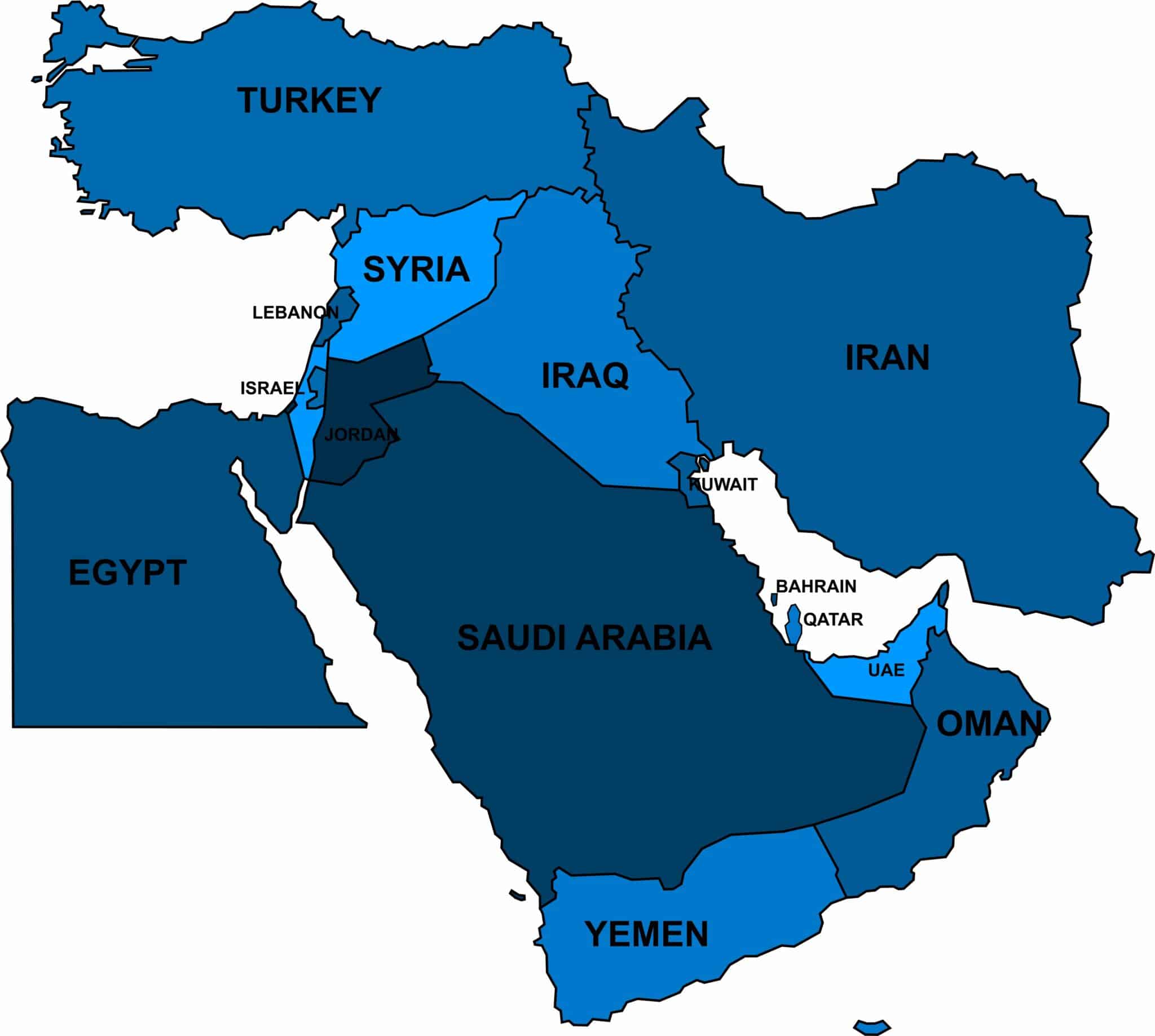
— Oil prices post weekly loss as market sees limited risk of wider war after Israel strike on Iran. — Retail sales surge 0.7% in March as Americans seem unfazed
Since the end of March, there has been a decided shift in market sentiment. LNW CIO Ron Albahary, CFA assesses what has changed and how we are keeping client portfolios on an
Over the weekend, the conflict in the Middle East reached a dangerously higher level. Iran launched an estimated 300 drones, ballistic and cruise missiles targeting Israel. Th
— U.S. consumer inflation ticked up in March to an annualized rate of 3.5% (3.8% excluding food and energy). The Fed is generally not expected to lower interest rates in
— The U.S. economy added a robust 303,000 new jobs in March and unemployment fell to 3.8%; job market strength makes it harder for Fed to lower interest rates. —
With U.S. stock markets near record highs, what we are doing to reduce risk. By David Baker, Senior Director, Investment Strategy and Communications.
Assets that appear most attractive to us on a risk-adjusted basis are those that help diversify equity risk.
— The U.S. economy grew a strong 3.4% annualized in 4th quarter 2023 (per latest estimate); a slowdown to 2.1% is expected for 1st quarter 2024. – U.S. manufactu
To his work as CIO of LNW, Ronald G. Albahary, CFA® brings more than 30 years of experience managing portfolios for high-net-worth and ultra-high-net-worth clients and