Intelligence
We invite you to browse our curated collection of insights and analysis — all developed by LNW team members.
Our Featured Content

Commentary Q1 2024: The Year of Momentous Elections
The more acute risks in the coming year are likely to be political and geopolitical, says LNW CIO Ron G. Albahary, CFA®. Find out how we are navigating an economic and market landscape of uncertainty, volatility and wider dispersion of potential outcomes. Click here for the Executive Summary or download full paper below.

Laird Norton Wetherby: A New Force in Wealth Management
“LNW is a testament to the aspirations of our clients, the talent and commitment of our team and the unwavering support of our owners.” — Kristen Bauer, CEO Today, January 11, marks a major milestone for our firm. We are very proud and excited to be coming together under the dynamic banner LNW (Laird Norton

Dual Citizenship: Planning for the Unpredictable Future
As the world becomes increasingly interconnected, dual citizenship can serve as both an insurance policy and a method of unlocking new opportunities.
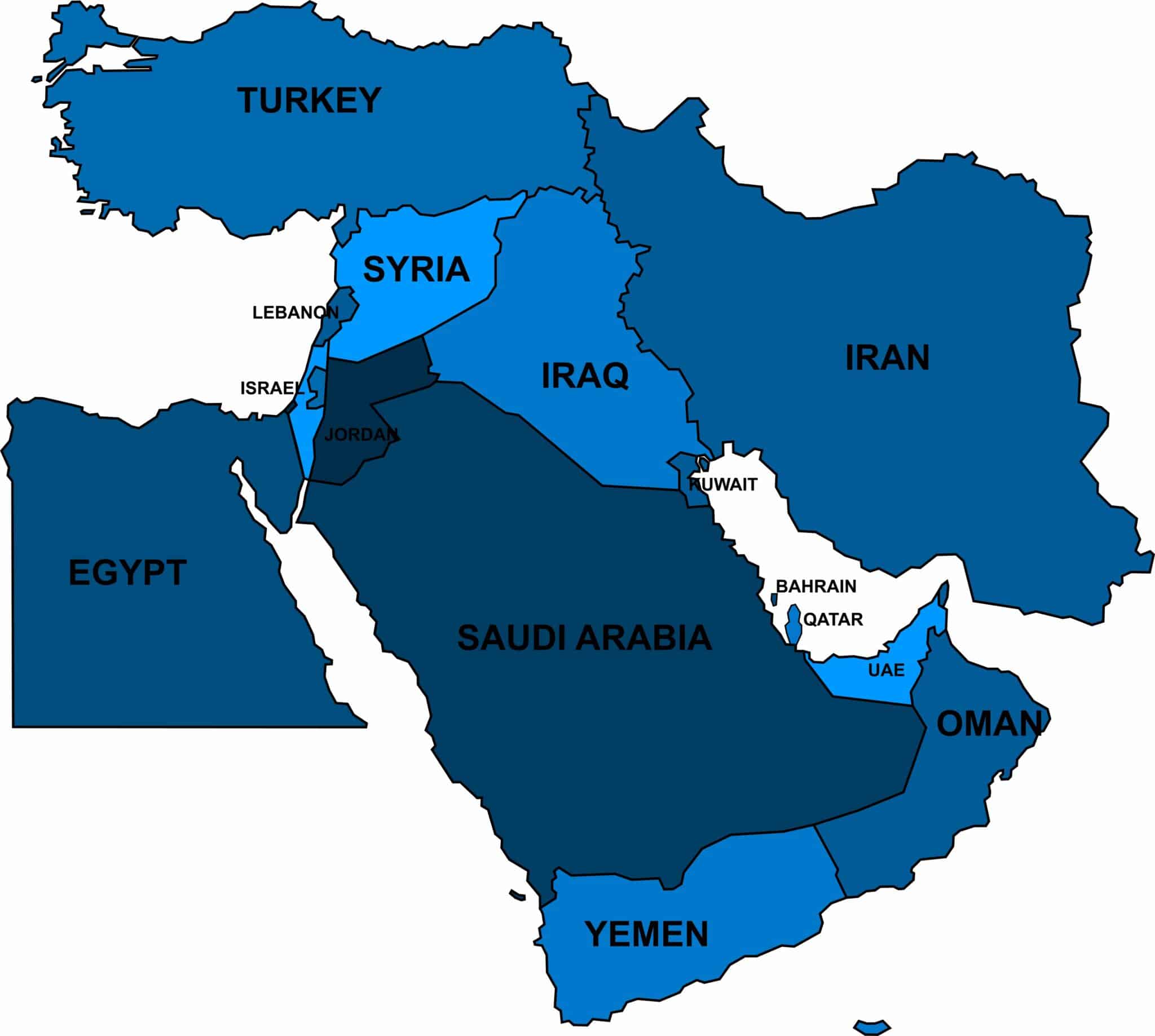
Over the weekend, the conflict in the Middle East reached a dangerously higher level. Iran launched an estimated 300 drones, ballistic and cruise missiles targeting Israel. Th
— U.S. consumer inflation ticked up in March to an annualized rate of 3.5% (3.8% excluding food and energy). The Fed is generally not expected to lower interest rates in
— The U.S. economy added a robust 303,000 new jobs in March and unemployment fell to 3.8%; job market strength makes it harder for Fed to lower interest rates. —
With U.S. stock markets near record highs, what we are doing to reduce risk. By David Baker, Senior Director, Investment Strategy and Communications.
Assets that appear most attractive to us on a risk-adjusted basis are those that help diversify equity risk.
— The U.S. economy grew a strong 3.4% annualized in 4th quarter 2023 (per latest estimate); a slowdown to 2.1% is expected for 1st quarter 2024. – U.S. manufactu
To his work as CIO of LNW, Ronald G. Albahary, CFA® brings more than 30 years of experience managing portfolios for high-net-worth and ultra-high-net-worth clients and
“Inflation is still high. The ongoing progress in bringing it down is not assured and the path forward is unsure.” — Fed Chair Jerome Powell, March 20 Press
— Federal Reserve holds rates steady and maintains three cuts coming sometime this year. — February home sales spike 9.5%, the largest monthly gain in a year, as s